
What is “Chain Email Reply Attack” and how it works?
An email account takeover is the first step in hijacking an email reply chain. Hackers gain access to one or more email accounts, either through an earlier compromise and credentials dumping or through techniques such as credential stuffing and password-spraying, and then begin monitoring conversation threads for opportunities to send malware or poisoned links to one or more of the participants in an ongoing chain of correspondence.
Because the beneficiaries have already created a sense of trust, the strategy is highly effective. The threat actor does not create a new correspondent or try to impersonate someone else’s email address. Rather, the attacker sends the infected email from one of the participants’ legitimate accounts.
The attacker can adapt their malspam message to fit the context of an existing conversation because they have access to the entire thread. This, combined with the fact that the recipient already trusts the sender, greatly enhances the likelihood that the victim will open the malicious attachment or click a harmful link.
Consider the following scenario: an account belonging to “Anil” has been hacked, and the attacker notices Anil and “Parul” (and possibly others) discussing a new sales campaign. The attacker can use this information to send Parul a malicious document that looks to be linked to their present conversation.
Hackers frequently utilise an alternative Inbox to receive messages in order to keep the owner of the hacked account unaware of the attacker’s actions.
This entails utilising the email client’s rules to direct specific messages away from the Inbox and into an area that the legitimate account user is unlikely to look at, such as the Trash folder. If Parul answers to Anil’s phishing email using this strategy, the reply can be routed such that the actual Anil never sees it.
When a hacker successfully takes control of an account, they can use the email client’s settings to transfer mail from specific recipients to another account.
Another method for keeping an account holder in the dark is to set up an email rule that scans incoming messages for phrases like “phish,” “phishing,” “hack,” and “hacked” and either deletes them or auto responds with a prefabricated message. This stops any suspicious or concerned co-workers from sending emails like “Have you been hacked?” and so on to the account holder.
What Malware Families Have Employed Reply Chain Attacks?
In 2017, email reply chain assaults first appeared. The approach was also employed by the Gozi ISFB/Ursnif banking trojan operations in 2018, while in some cases the chain of correspondence was merely forged to add validity; in others, the attackers hacked legitimate accounts and used them to hijack existing threads and spam other recipients.
Malicious attachments may use Office Macros to transmit payloads like Emotet, Ursnif, and other loader or banking trojan software using VBScript and PowerShell and once opened will look like this.
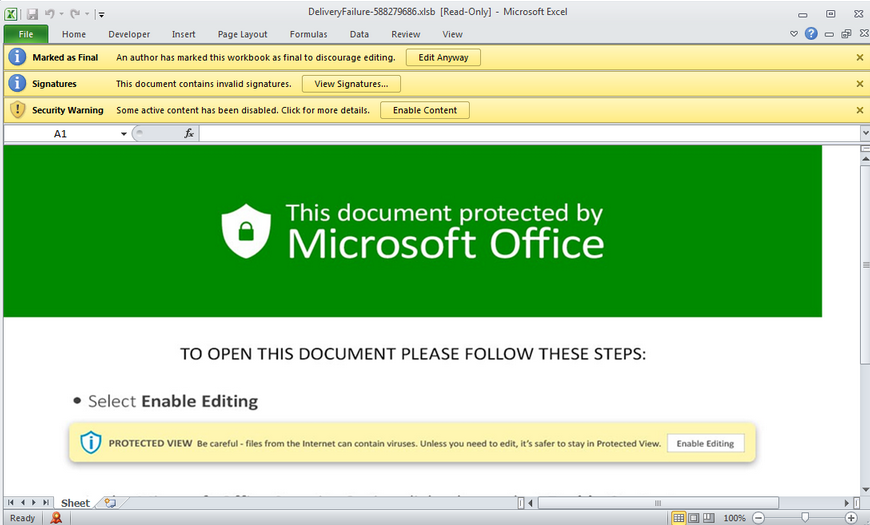
Valak virus includes specialised plugins built to steal credentials exclusively for use in email reply chain attacks, according to researchers.
Why do email reply chain attacks work so well?
Although spear phishing and even blanket spam phishing efforts are still popular among threat actors, email reply chain attacks significantly raise the bar for defences.
Furthermore, mass spoofing emails sometimes have subjects or body messages that are unrelated to the majority of recipients, immediately arousing suspicion.
Even in the case of more targeted spear phishing attacks, awareness training and safe email practises like not clicking links, opening attachments from unknown senders, and replying to unwelcome emails can help reduce risk. The normal types of warning flags may be missing in email reply chain attacks.
The most cautious and well-trained employees are vulnerable to email reply chain attacks, which are often carefully crafted with no language errors. The credibility gained by inserting a reply to an existing thread from a legitimate sender means that even the most cautious and well-trained staff are at risk of falling victim to this type of tactic.
How can a reply chain attack be prevented?
A well-crafted reply chain assault can be difficult to identify, especially if it appears in (or appears to be part of) a long thread with several, trusted participants, given their trusted, genuine point of origin and the fact that the attacker possesses email history and conversational context.
There are, however, numerous steps you may take to avoid becoming a victim of this form of fraud.
First and foremost, because reply chain attacks rely on account breaches, make sure that all of your company’s email accounts are secure. Two-factor or multi-factor authentication, unique passwords for each account, and passwords of at least 16 characters are all required. Users should be urged to check their email client settings and mail rules on a frequent basis to ensure that mails are not being redirected or deleted without their knowledge.
Second, wherever possible, restrict or prohibit the usage of Office macros. Malicious attachments can compromise a device in a variety of ways, but macros are still a common attack vector.
Third, knowledge is power, so include a discussion of email reply chain assaults and how they work in your user awareness training by directing employees to publications like this one. Email users should be more aware of how phishing attempts work and how attackers’ tactics are improving. They must also comprehend why, regardless of the source, all requests to open attachments or click links should be treated with caution.
Fourth, and most critically, make sure your endpoints are protected with a contemporary, reliable EDR security solution that can prevent malicious code concealed in attachments or links from executing and causing damage. Traditional antivirus suites based on reputation and YARA rules were not designed to address contemporary, fileless, and polymorphic threats. In today’s cyber security threat landscape, a next-generation, automated AI-powered platform is the bare minimum.
Conclusion
Threat actors use email reply chain attacks as another method of social engineering to achieve their objectives. In contrast to the physical world, which has hardcoded laws of nature, the cyber world has no rules that cannot be changed by changing the hardware, software, or the user. This, however, is true for both defenders and attackers. We can defeat attacks before they occur or cause long-term damage to the organisation if we maintain control over all parts of our cyber environment. Secure your devices, educate your users, train your employees, and let the fraudsters look for another victim.
Share This post!

What is “Chain Email Reply Attack” and how it works?
An email account takeover is the first step in hijacking an email reply chain. Hackers gain access to one or more email accounts, either through an earlier compromise and credentials dumping or through techniques such as credential stuffing and password-spraying, and then begin monitoring conversation threads for opportunities to send malware or poisoned links to one or more of the participants in an ongoing chain of correspondence.
Because the beneficiaries have already created a sense of trust, the strategy is highly effective. The threat actor does not create a new correspondent or try to impersonate someone else’s email address. Rather, the attacker sends the infected email from one of the participants’ legitimate accounts.
The attacker can adapt their malspam message to fit the context of an existing conversation because they have access to the entire thread. This, combined with the fact that the recipient already trusts the sender, greatly enhances the likelihood that the victim will open the malicious attachment or click a harmful link.
Consider the following scenario: an account belonging to “Anil” has been hacked, and the attacker notices Anil and “Parul” (and possibly others) discussing a new sales campaign. The attacker can use this information to send Parul a malicious document that looks to be linked to their present conversation.
Hackers frequently utilise an alternative Inbox to receive messages in order to keep the owner of the hacked account unaware of the attacker’s actions.
This entails utilising the email client’s rules to direct specific messages away from the Inbox and into an area that the legitimate account user is unlikely to look at, such as the Trash folder. If Parul answers to Anil’s phishing email using this strategy, the reply can be routed such that the actual Anil never sees it.
When a hacker successfully takes control of an account, they can use the email client’s settings to transfer mail from specific recipients to another account.
Another method for keeping an account holder in the dark is to set up an email rule that scans incoming messages for phrases like “phish,” “phishing,” “hack,” and “hacked” and either deletes them or auto responds with a prefabricated message. This stops any suspicious or concerned co-workers from sending emails like “Have you been hacked?” and so on to the account holder.
What Malware Families Have Employed Reply Chain Attacks?
In 2017, email reply chain assaults first appeared. The approach was also employed by the Gozi ISFB/Ursnif banking trojan operations in 2018, while in some cases the chain of correspondence was merely forged to add validity; in others, the attackers hacked legitimate accounts and used them to hijack existing threads and spam other recipients.
Malicious attachments may use Office Macros to transmit payloads like Emotet, Ursnif, and other loader or banking trojan software using VBScript and PowerShell and once opened will look like this.

Valak virus includes specialised plugins built to steal credentials exclusively for use in email reply chain attacks, according to researchers.
Why do email reply chain attacks work so well?
Although spear phishing and even blanket spam phishing efforts are still popular among threat actors, email reply chain attacks significantly raise the bar for defences.
Furthermore, mass spoofing emails sometimes have subjects or body messages that are unrelated to the majority of recipients, immediately arousing suspicion.
Even in the case of more targeted spear phishing attacks, awareness training and safe email practises like not clicking links, opening attachments from unknown senders, and replying to unwelcome emails can help reduce risk. The normal types of warning flags may be missing in email reply chain attacks.
The most cautious and well-trained employees are vulnerable to email reply chain attacks, which are often carefully crafted with no language errors. The credibility gained by inserting a reply to an existing thread from a legitimate sender means that even the most cautious and well-trained staff are at risk of falling victim to this type of tactic.
How can a reply chain attack be prevented?
A well-crafted reply chain assault can be difficult to identify, especially if it appears in (or appears to be part of) a long thread with several, trusted participants, given their trusted, genuine point of origin and the fact that the attacker possesses email history and conversational context.
There are, however, numerous steps you may take to avoid becoming a victim of this form of fraud.
First and foremost, because reply chain attacks rely on account breaches, make sure that all of your company’s email accounts are secure. Two-factor or multi-factor authentication, unique passwords for each account, and passwords of at least 16 characters are all required. Users should be urged to check their email client settings and mail rules on a frequent basis to ensure that mails are not being redirected or deleted without their knowledge.
Second, wherever possible, restrict or prohibit the usage of Office macros. Malicious attachments can compromise a device in a variety of ways, but macros are still a common attack vector.
Third, knowledge is power, so include a discussion of email reply chain assaults and how they work in your user awareness training by directing employees to publications like this one. Email users should be more aware of how phishing attempts work and how attackers’ tactics are improving. They must also comprehend why, regardless of the source, all requests to open attachments or click links should be treated with caution.
Fourth, and most critically, make sure your endpoints are protected with a contemporary, reliable EDR security solution that can prevent malicious code concealed in attachments or links from executing and causing damage. Traditional antivirus suites based on reputation and YARA rules were not designed to address contemporary, fileless, and polymorphic threats. In today’s cyber security threat landscape, a next-generation, automated AI-powered platform is the bare minimum.
Conclusion
Threat actors use email reply chain attacks as another method of social engineering to achieve their objectives. In contrast to the physical world, which has hardcoded laws of nature, the cyber world has no rules that cannot be changed by changing the hardware, software, or the user. This, however, is true for both defenders and attackers. We can defeat attacks before they occur or cause long-term damage to the organisation if we maintain control over all parts of our cyber environment. Secure your devices, educate your users, train your employees, and let the fraudsters look for another victim.





